Edward Snowden's tips to protect our privacy
Ever since 2013, the entire world has changed due to the revelations of dozens of global surveillance programs made by former agent Edward Snowden which were hidden by the NSA. We have seen a change in methods of security by applications and privacy policies made by internet companies. More and more people to this day are now raising questions about how their data is being handled and who are they actually giving it to. And it’s all thanks to this man. But just who is Edward Snowden and what does he actually intend to do?
Who is Edward Snowden?
Edward Snowden was a former CIA employee who also worked as an NSA subcontractor at a facility in Hawaii during the leak periods of 2013. He comes from a background of government officials and officers, his family having all worked with them: his grandfather was a rear admiral and senior official at the FBI, his father worked as an officer, his mother was a clerk and his sister was a lawyer.
Before Snowden worked with the CIA, he tried to join the US Special Forces in 2004 to help fight the Iraq War, but he failed to complete the training due to an injury he got during his time there. After that he worked as a security guard for University of Maryland at a research center sponsored by the NSA in 2005.
Then he became a CIA agent after he attended a job-fair focused on intelligence agencies in 2006. He stopped working for them in 2009 and was hired by Dell to manage computer systems for multiple government agencies. And then in 2013, he was assigned to a NSA facility in Hawaii after having worked with Dell.


2013 Global Surveillance Leaks

Snowden was hired by NSA contractor, Booz Allen Hamilton in 2013 after having previously worked with Dell and the CIA and started to work at a facility in Hawaii. It was there that Snowden found out about the global surveillance programs that the NSA had kept secret from everyone.
He became gradually disillusioned with what he was involved in and started raisng ethical concerns about this. Snowden tried to warn everyone about the practices the NSA were doing through internal channels but was completely ignored.
And so, he leaves his job and on May 20 2013, he leaves Hawaii for Hong Kong where he would only stay for a few weeks.

In early June, Edward Snowden takes an interview with the journalists from The Guardian and The Washington Post, specifically Glenn Greenwald, Laura Poitras and Ewen MacAskil, in which he revealed the infamous global surveillance programs to the world.
The most notorious of those programs were PRISM and XKeyScore. They were data collection programs that had access to almost all of the information that the internet had.
They were even able to look through even the most private and intimate data and they were used to analyze through that information and take away the very important bits of what they have collected.


After he exposed NSA’s secrets to the world, Snowden had fled to Russia and took asylum there and the USA started to condemn him, assign charges against him and take away his passport.
Current situation as of today
Right now, Snowden currently is still in asylum in Russia. His permit to stay is expiring in 2020 and he plans to extend it for 3 more years, but no one knows if he’s still allowed to stay or not.
His autobiography was also published on September 2019 called “Permanent Record” in which he talks more about his life and what was his work like at the CIA and NSA, more about his reasons for why he decided to leak everything and destroy his career for this and he talks more about his political views and what he believes in.
On August 15 2020, Trump said that he will look more into the Snowden case and might consider pardoning him, although it isn’t really sure if that would be the case since the president was also against him in the past. The current situation is still unknown and the president hasn’t said anything since then.
On September 3 2020, the NSA mass surveillance programs exposed by Edward Snowden was ruled illegal by the US court although he still faces charges of espionage and no one knows what their stance is still.

What is Snowden doing now?
Edward Snowden became president of the Freedom of the Press Foundation (FPF) on September 2016. They’re organization that supports freedom of speech and the freedom of the press. Its purpose is to protect journalists from hacking and government surveillance. They are very caring about privacy and because of this, they have affiliated with the Electronic Frontier Foundation (EFF).
The EFF are an organization which seeks to promote internet civil liberties. Such liberties include: user privacy, freedom of expression, using free and open source software etc. Basically, they’re an organization that fights for the freedom of the user on the internet that also believes privacy is a human right.
Snowden along with these organizations fight against global surveillance and for privacy of the individual by giving numerous talks on why it is very important to protect it. He gives us numerous tips on how to improve our privacy and to escape from surveillance as much as possible.


We are going to be covering the most important ones that you should take in consideration when using your computer such that at the end of the day, you will have more security measures when browsing the web or using your computer for certain things:
Privacy tips from Snowden
Tip #1 – Encrypt your Hard Drive
The first tip we are going to discuss about is related to encryption, specifically encrypting your hard drive. Snowden talks a lot about encryption and why it’s very important to use it. It’s to protect our personal data from those wish to steal or snoop upon them. This also means that you should encrypt absolutely everythign that you consider private to you and wouldn’t want to be compromised. For this, Snowden also says that encrypting your hard drive is very important. He says that:
“You should encrypt your hard disk, so that if your computer is stolen the information isn’t obtainable to an adversary — pictures, where you live, where you work, where your kids are, where you go to school.”
And not only that. If, let’s say your laptop does get stolen by some burglar, you basically gave him access to absolutely everything that you own: your photos, your e-mail, your passwords, your messages, your credit card number and so on and so forth. You have basically given away all that information for free and no one would want to have that happen to them.
So, encrypting your hard drive ensures your personal data stays secure, even if your device has been stolen or seized by someone. You can do this on any operating system you want:



Windows has a built-in feature called Bitlocker which you can use to encrypt your hard drive. For other operating systems such as Mac, there is FileVault and for Linux, there is LUKS. Although, LUKS is more for people who have a bit of an experience with Linux.
It’s really encouraged to do this thing as it adds a big security feature to your computer and your personal data won’t be revealed if your laptop gets stolen.
Tip #2 – Encrypt your Text messages and Calls
The second tip we’ll talk about is also related to encryption, specifically text messages and calls. Encryption, as Snowden said, is incredibly important and it shouldn’t be limited to a single thing, it should be on everything you consider private to you, including your text messages and calls.
What Snowden recommends for such a thing is the app called Signal, saying that:

“The first step that anyone could take is to encrypt their phone calls and their text messages. You can do that through the smartphone app Signal, by Open Whisper Systems. It’s free, and you can just download it immediately. And anybody you’re talking to now, their communications, if it’s intercepted, can’t be read by adversaries.”
Signal is way better and way more secure than WhatsApp, as WhatsApp isn’t necessarily to be trusted. Their source code is proprietary and it’s also owned by Facebook, which is guaranteed to collect your data from WhatsApp. On the other hand, Signal is free and open source and the code can be viewed and reviewed by anyone who wishes to look into it. WhatsApp even says that it uses their protocol to encrypt the messages so it’s quite trustworthy. If you care about not having your conversations leaked or given away for someone to read, definitely use Signal and ditch WhatsApp.
While we are at it, we can also give you a few recommendations if you are looking for better alternatives on apps that you are using:
For example, if you perhaps use Discord, a good alternative would be Element. It’s open source and you can host your own encrypted server without relying on anyone.
You can chat, share images just as you would on Discord, but there is a big drawback which is that there are currently no voice channels included in the app. They are still working on it to implement the feature. In the meantime, it’s still a good alternative if you perhaps just want to chat or work with your team on stuff.

Other alternatives would be Briar and Jami. They’re encrypted messengers just like Signal, except that you do not have to rely on a server to talk and speak to your friends and you can just talk to them directly phone-to-phone or computer-to-computer using P2P technology.


Tip #3 – Avoid online tracking with browser plugins
The third tip Snowden also talks about is browser plugins. There are plugins that enhance your privacy and make you avoid online tracking from internet companies. A very important plugin that most of you probably have is an adblocker. Snowden states that:
“Everybody should be running adblock software, if only from a safety perspective”
The reason he says that is because advertisers and brands use your Google searches to attract you with their deals. If you search for example, a new laptop for yourself, they will collect that search and whenever you visit a big shopping website, such as Amazon, they will give you an ad with the laptop that you wish to buy. They know what you want to buy before you even access the website and you sold them your data because of this. That is why you need to use an adblocker as it will give you more safety when looking for things. What we recommend is the addon called uBlock Origin and you can install it right now on your browser.
Another great plugin which is made by the EFF is called HTTPS Everywhere. It encrypts all the connections to the website you wish to go to by adding HTTPS instead of HTTP at the URL. It makes it very difficult for an eavesdropper to look at what you are doing on the website. Snowden even states that:
“If you use browser plugins like HTTPS Everywhere by EFF, you can try to enforce secure encrypted communications so your data is not being passed in transit electronically naked.”
There are plenty of other good plugins you can use, but these are the most important ones that should be in every single browser when looking through the internet.


Tip #4 – Online anonymity
A tip that you might consider to be a bit controversial is regarding online anonymity. The reasion it might be like that is because Snowden talks about being anonymous on the internet and how we can achieve that using Tor:
“I think Tor is the most important privacy-enhancing technology project being used today. I use Tor personally all the time.[…]What Tor does is it provides a measure of security and allows you to disassociate your physical location.”
Let’s get something straight here: Tor is NOT illegal to use! You are not a criminal if you use Tor or if you browse any website you wish to look for with Tor. It’s only illegal if you live in an authoritarian country such as China or North Korea. Sure, Tor is more known for hosting criminal activity there, but that isn’t it’s purpose.

Tor was designed specifically to give you anonymity on the internet and to circumvent censorship from governments. Your ISP can’t see what you are doing on Tor and you can browse any website just as you normally would without being a criminal. It gives you that extra layer of security and it’s better than a VPN in the sense that you pass through more servers than just one server and that everyone can run their own Tor server/node, which makes it even more secure:
“But the basic idea, the concept of Tor that is so valuable, is that it’s run by volunteers. Anyone can create a new node on the network, whether it’s an entry node, a middle router, or an exit point, on the basis of their willingness to accept some risk. The voluntary nature of this network means that it is survivable, it’s resistant, it’s flexible.”
If you want to browse the web without anyone knowing what you are browsing, Tor is the perfect choice to do so. You can start using Tor by downloading the Tor Browser from their website.
Tip #5 – Avoid services like Google, Facebook and Dropbox
Another tip Snowden talks about is obviously avoiding services like Google, Facebook, Dropbox and etc. Reason for that is pretty well known, as these companies track your every search, every image that you post, every like that you give etc. They infiltrate your private life without your consent and use it for their own gains:
“Facebook’s internal purpose, whether they state it publicly or not, is to compile perfect records of private lives to the maximum extent of their capability, and then exploit that for their own corporate enrichment.[…]Google … has a very similar model.”
So,



If you look for an alternative for searches on Google, DuckDuckGo is a much better choice. As for social media, we do not have a better alternative currently.
You should avoid cloud services like Dropbox since they snoop upon what you store on servers:
“Dropbox is a targeted you know wannabe PRISM partner[…],so they’re very hostile to privacy.”
If you want a good cloud host that respects your privacy more, use a host that uses the software Nextcloud as it is open-source and much more secure than Dropbox.


Tip #6 – Create stronger passwords (or passphrases)
One tip that is absolutely crucial to take in consideration are passwords. Having strong passwords is essential to having a secure account and make it hard for the hacker to crack it. Snowden talks about what it means to have bad passwords and states that:
“Bad passwords are one of the easiest ways to compromise a system. For somebody who has a very common 8 character password, it can literally take less than a second for a computer to go through the possibilities and pull that password out”
It doesn’t matter how many special characters or digits your password has, the computer is capable of cracking the password in days, minutes or even seconds if your password is weak in terms of character length. We placed here a little comic that explains what it means to have good passwords.
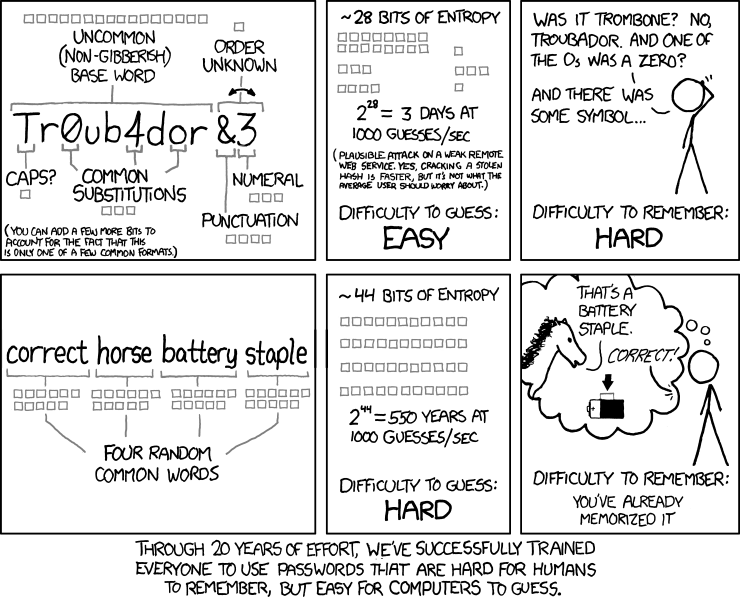
For example, a complicated password with random letters and numbers isn’t gonna help you and can be easily cracked if a hacker has the dedicated time for this. Not only that, passwords like these are very hard to remember and can easily be forgotten if you are not careful. That is why Snowden says we should switch from thinking in passwords to passphrases. What this means is that you can have a phrase as your password or a set of words tied in together and have the password become a million times better. If you have a set of words such as the password on the bottom of the comic, you already have a stronger password as it has many characters and it would take a computer hundreds of years to crack it. And you don’t even need digits or special characters at all!
So, if you want a strong set of words but you don’t have any idea what to put in your password, we recommend watching a video from Computerphile about Diceware. It’s a fun little minigame where you choose your password simply by throwing your dice and it generates a truly random password for your account.
Tip #7 – Use a password manager
Another tip that must be taken in consideration is that you have to use a password manager to make your accounts more secure. DO NOT use the same password for absolutely every website that you go to as it is bad practice to do and you can get your accounts easily hacked if a company gets hacked and their database gets leaked:
“Use a password manager. One of the main things that gets people’s private information exposed, not necessarily to the most powerful adversaries, but to the most common ones, are data dumps. Your credentials may be revealed because some service you stopped using in 2007 gets hacked, and your password that you were using for that one site also works for your Gmail account. A password manager allows you to create unique passwords for every site that are unbreakable, but you don’t have the burden of memorizing them.”
Your account can get easily compromised and you can potentially lose all of your data. So password managers avoid you to have the same password and increase the security of your account by creating unbreakable passwords for each website that you browse.
We recommend using KeePassXC as it is a very good open-source password manager and can be used on all operating systems, including Windows, MacOS and Linux.

Tip #8 – Use two-factor authentication
Using two-factor authentication is a nice security feature to have as this is a plan B if your account might get compromised because someone found your password. Snowden states that:
“The other thing there is two-factor authentication. The value of this is if someone does steal your password, or it’s left or exposed somewhere … [two-factor authentication] allows the provider to send you a secondary means of authentication — a text message or something like that.”
You will never know what can happen to your account, so having your cellphone or e-mail account to use for authentication can make your account much safer than it is.

CONCLUSION
We would like to say that without Snowden, we probably would have ended up in bigger trouble than we are now. We would be continuously spied on by government agencies and have all these companies infiltrate our private lives without our consent.
Him revealing everything made the world much more aware of what was happening now. The least we could do is take all of these tips in consideration and be very careful to who we give our data. We need to protect ourselves from any malicious threat by increasing our security and we mustn’t trust any service at first. Always research first and check their background to see if they are clean or not.
